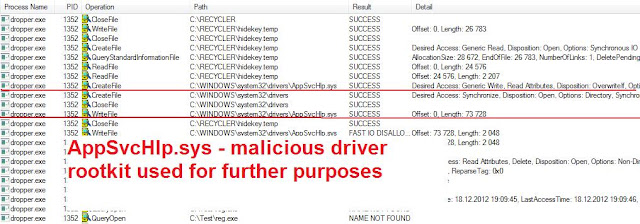
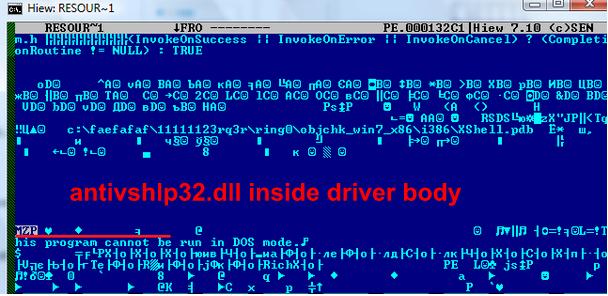
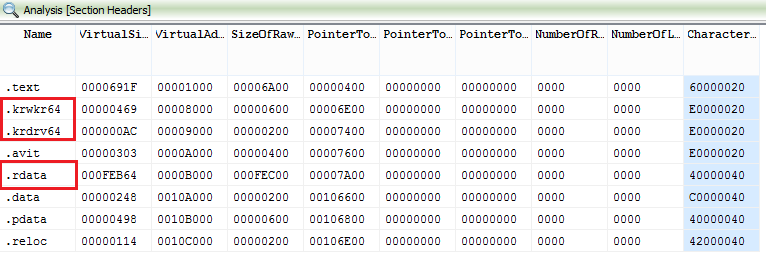
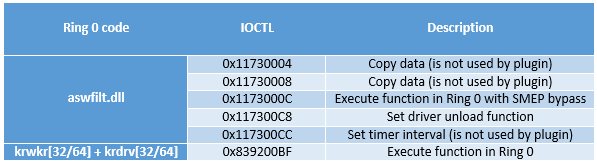
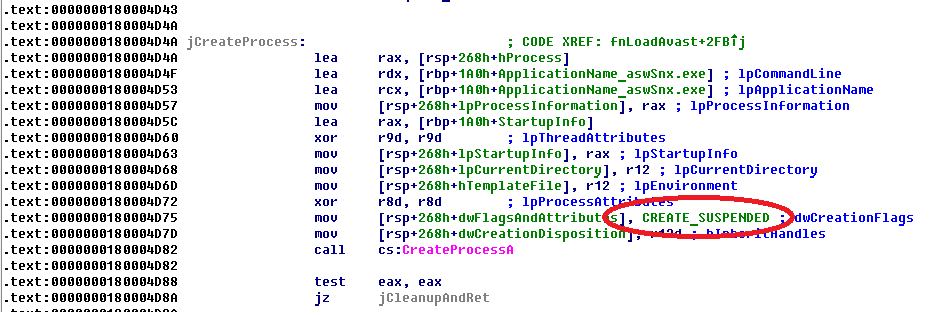
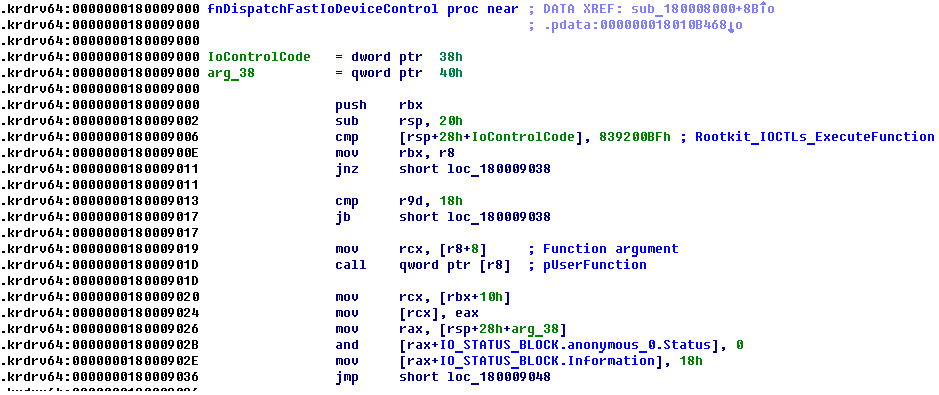
Original dropper that contains bootkit dropper:
SHA1: e83ca87a39a5f15ca5942fd57d78e790861c2937
MD5: 15e692cf34a70fb364591622bff1e43a
File size: 86027 bytes
This original dropper extracts bootkit dropper from itself and launches it on execution with same name.
Bootkit dropper:
SHA1: 5ecefefe4bbfc040927e827ab81c10caf5d10f90
MD5: f72e3d86b8f4f97d103ff1b7f87213f2
File size: 54272 bytes
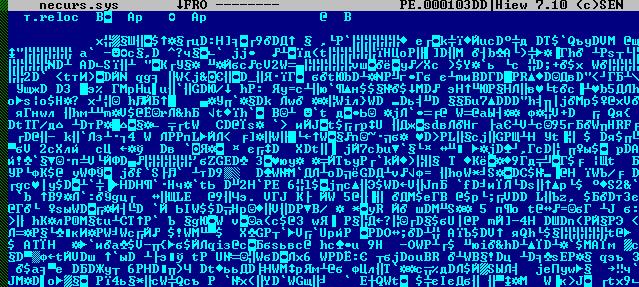
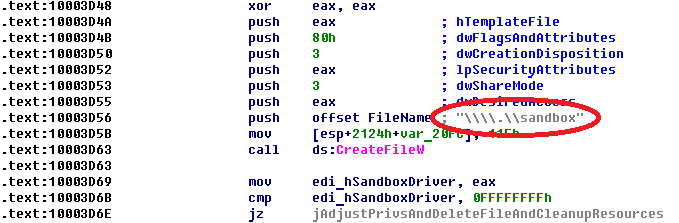
Bootkit dropper stores it components in resource section in crypted state.
Decryption routine has view:
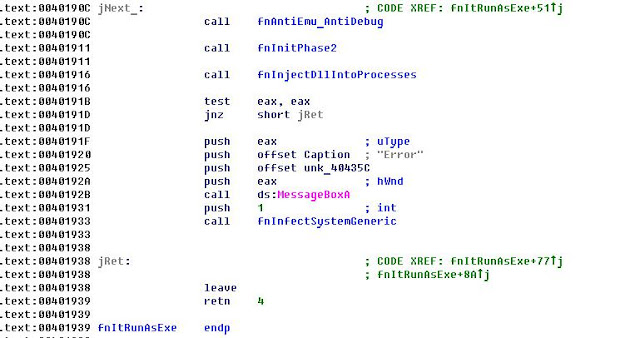
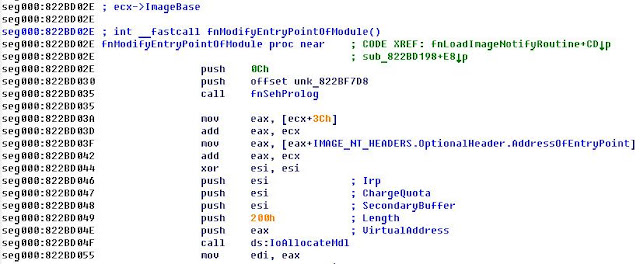
Bootkit dropper has an interesting method of calling OEP via SEH handler with generating an exception.
OEP has view (dropper supports two modes of running - as dll and exe).
Anti-debug/anti-emu feature:
On the next stage it performs an interesting trick to load itself via dll and continuing initialization as dll.
In the first, it copies itself to system directory with random name.tmp and patches PE-characteristics by setting Dll flag.
In the second, it hooks imm32.dll!ImmLoadLayout and ntdll.dll!ZwQueryValueKey.
ZwQueryValueKey hook has view:
After hooks were set it tries initiate keyboard layout switching (that was already registered via creating new parameter in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Keyboard Layouts). Malicious keyboard layout has view:
Finally revert layout to original.
Second stage initialization via dll loading.
At this stage dll should be loaded into working processes in system and first that it does - sets special event to signal bootkit exe dropper about success of running.
So, if injection was failed, it runs next phase.
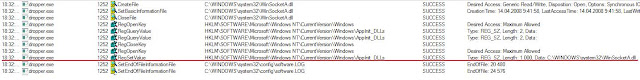
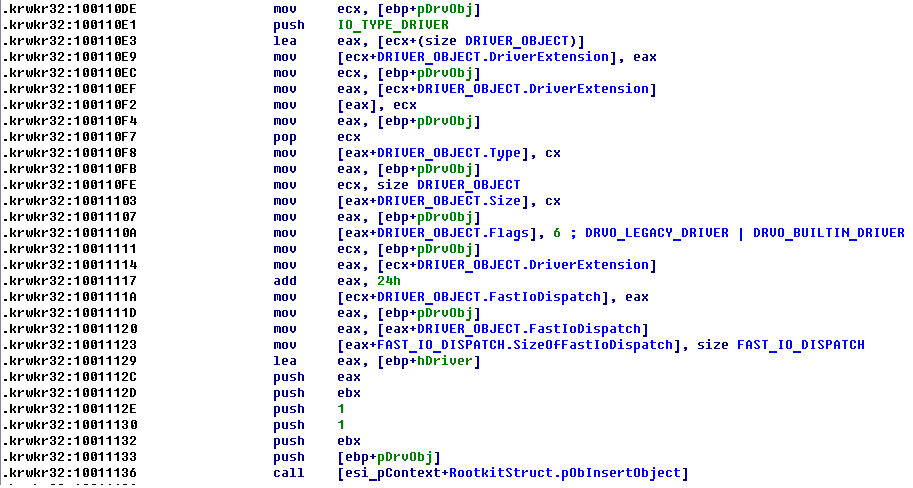
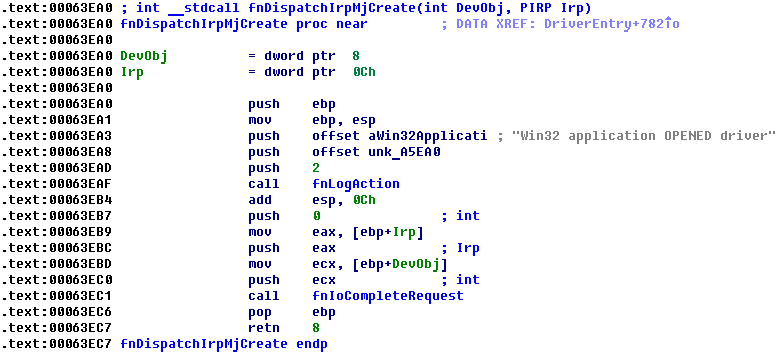
Before load it's driver, it performs some actions targeted to disable some protections that can present in the system.
- In case of HintClient.exe that belongs to company Shanghai Hintsoft Co.,LTD. - http://www.hintsoft.com.cn/ sends a special IOCTL code to it driver (look code at 00403A3B).
- In case of Drvmon (drivers monitoring tool) also sends a special IOCTL to unknown driver (look code at 00403B0A).
![]()
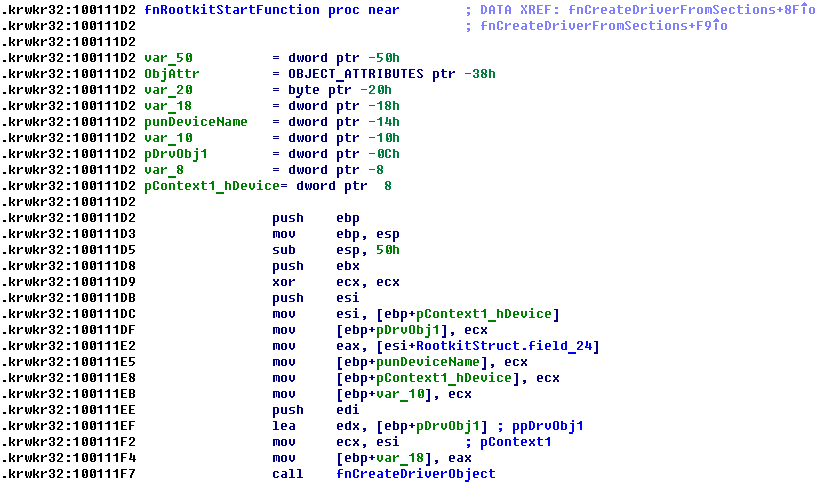
Next it loads driver and infects MBR.
Driver:
SHA1: adcdee632d7915f5e73669d809d9713e9250b81d
MD5: c1f5c5af49243e497ae979f2622ab5d0
File size: 4704 bytes
Features of driver:
- Low-level disk I/O
- Processes killlig
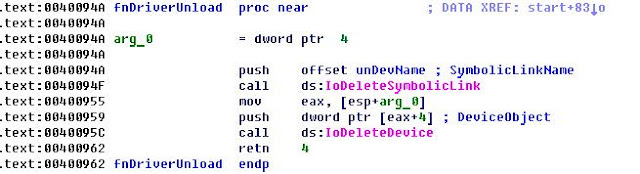
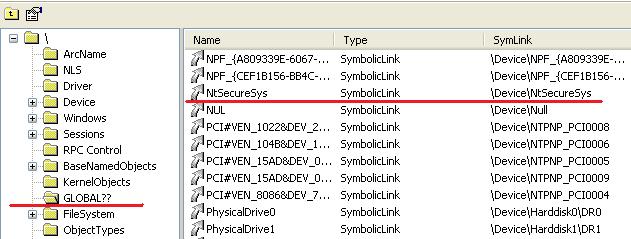
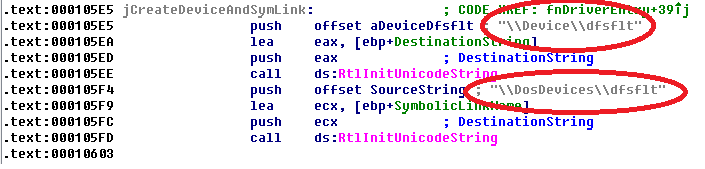
Creates device with name \Device\Guntior for communicate with ring3.
\Device\Guntior
\??\Guntior
RSDS
C:\sys.pdb
memcpy
MmMapLockedPagesSpecifyCache
memset
IoDeleteSymbolicLink
RtlInitUnicodeString
IoDeleteDevice
RtlGetVersion
IofCompleteRequest
IoCreateSymbolicLink
IoCreateDevice
PsLookupProcessByProcessId
MmIsAddressValid
ObfDereferenceObject
ObReferenceObjectByPointer
ntoskrnl.exe
WRITE_PORT_BUFFER_USHORT
HalGetBusData
READ_PORT_BUFFER_USHORT
KfRaiseIrql
KfLowerIrql
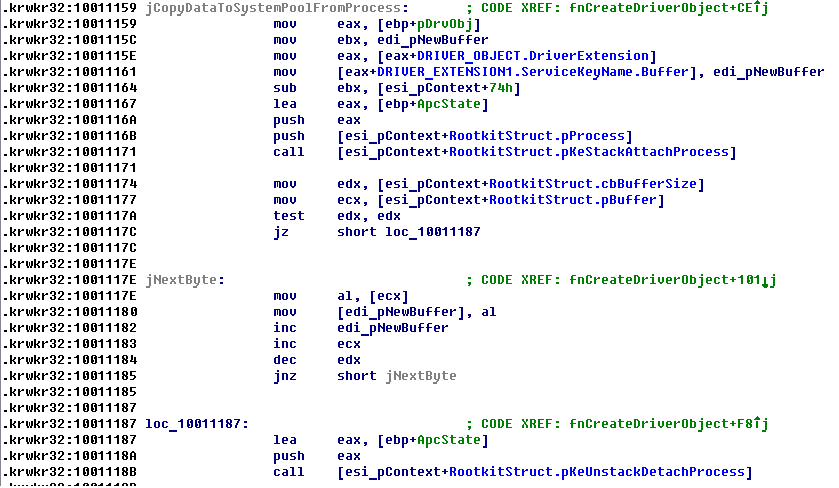
Killing processes code:
Dropper with decrypted payload available for download here:
http://www.kernelmode.info/forum/viewtopic.php?f=16&t=1765#p14683
Dumps of malicious code with some comments by Peter here:
http://www.kernelmode.info/forum/viewtopic.php?f=16&t=1765#p14709
Enjoy.
SHA1: e83ca87a39a5f15ca5942fd57d78e790861c2937
MD5: 15e692cf34a70fb364591622bff1e43a
File size: 86027 bytes
This original dropper extracts bootkit dropper from itself and launches it on execution with same name.
Bootkit dropper:
SHA1: 5ecefefe4bbfc040927e827ab81c10caf5d10f90
MD5: f72e3d86b8f4f97d103ff1b7f87213f2
File size: 54272 bytes
Bootkit dropper stores it components in resource section in crypted state.
Decryption routine has view:
Bootkit dropper has an interesting method of calling OEP via SEH handler with generating an exception.
OEP has view (dropper supports two modes of running - as dll and exe).
Anti-debug/anti-emu feature:
On the next stage it performs an interesting trick to load itself via dll and continuing initialization as dll.
In the first, it copies itself to system directory with random name.tmp and patches PE-characteristics by setting Dll flag.
In the second, it hooks imm32.dll!ImmLoadLayout and ntdll.dll!ZwQueryValueKey.
ZwQueryValueKey hook has view:
After hooks were set it tries initiate keyboard layout switching (that was already registered via creating new parameter in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Keyboard Layouts). Malicious keyboard layout has view:
Finally revert layout to original.
Second stage initialization via dll loading.
At this stage dll should be loaded into working processes in system and first that it does - sets special event to signal bootkit exe dropper about success of running.
So, if injection was failed, it runs next phase.
Before load it's driver, it performs some actions targeted to disable some protections that can present in the system.
- In case of HintClient.exe that belongs to company Shanghai Hintsoft Co.,LTD. - http://www.hintsoft.com.cn/ sends a special IOCTL code to it driver (look code at 00403A3B).
- In case of Drvmon (drivers monitoring tool) also sends a special IOCTL to unknown driver (look code at 00403B0A).

Next it loads driver and infects MBR.
Driver:
SHA1: adcdee632d7915f5e73669d809d9713e9250b81d
MD5: c1f5c5af49243e497ae979f2622ab5d0
File size: 4704 bytes
Features of driver:
- Low-level disk I/O
- Processes killlig
Creates device with name \Device\Guntior for communicate with ring3.
\Device\Guntior
\??\Guntior
RSDS
C:\sys.pdb
memcpy
MmMapLockedPagesSpecifyCache
memset
IoDeleteSymbolicLink
RtlInitUnicodeString
IoDeleteDevice
RtlGetVersion
IofCompleteRequest
IoCreateSymbolicLink
IoCreateDevice
PsLookupProcessByProcessId
MmIsAddressValid
ObfDereferenceObject
ObReferenceObjectByPointer
ntoskrnl.exe
WRITE_PORT_BUFFER_USHORT
HalGetBusData
READ_PORT_BUFFER_USHORT
KfRaiseIrql
KfLowerIrql
Driver is a loaded via very interesting trick with sending a special IOCTL to PnpManager.
Unlike other bootkits that intercept functions of disk.sys or atapi.sys for hiding malicious MBR and payload in the end of the disk, this bootkit intercepts nothing and supports unloading (it has an unloading routine).
Original (not-infected) MBR has view:
Malicious (by 0x190 offset it stores offset of its extension):
It also completely rewrites systemroot\system32\sfc_os.dll by dll body.
![]()
![]()
Dll targeted to killing processes:
nod32krn.exe
egui.exe
ekrn.exe
360tray.exe
360leakfixer.exe
360Safe.exe
safeboxTray.exe
360safebox.exe
360sd.exe
ZhuDongFangYu.exe
360rp.exe
360sdupd.exe
Calc.exe
KSWebShield.exe
kxesapp.exe
kxeserv.exe
kwstray.exe
kxedefend.exe
upsvc.exe
kxescore.exe
KVExpert.exe
kxetray.exe
KSafeSvc.exe
KSafeTray.exe
guiyingfix.exe
RavMonD.exe
RsTray.exe
RsAgent.exe
RegGuide.exe
RsMain.exe
RsCopy.exe
Rav.exe
KVSrvXP.exe
KVExpert.exe
KVMonXp.exe
avp.exe
avp.exe
ras.exe
knownsvr.exe
rstray.exe
knsdtray.exe
knsd.exe
knsdsvc.exe
knsdsve.exe
QQPCLeakScan.exe
QQPCWebShield.exe
QQPCTAVSrv.exe
QQPCRTP.exe
QQPCMgr.exe
QQPCUpdateAVLib.exe
QQPCTray.exe
QQRepair.exe
QQPCPatch.exe
In the end of disk bootkit stores:
- Original MBR
- Extension of malicious boot-code
- Dll
- Driver
Main payload is stored into dll [resource number 111]. Dropper extracts it from resource, decrypts and writes into systemroot\system32\appmgmts.dll.
It also completely rewrites systemroot\system32\sfc_os.dll by dll body.
Internally dll stored as rewritten sfc_os.dll from Chinese Windows XP.


Dll targeted to killing processes:
nod32krn.exe
egui.exe
ekrn.exe
360tray.exe
360leakfixer.exe
360Safe.exe
safeboxTray.exe
360safebox.exe
360sd.exe
ZhuDongFangYu.exe
360rp.exe
360sdupd.exe
Calc.exe
KSWebShield.exe
kxesapp.exe
kxeserv.exe
kwstray.exe
kxedefend.exe
upsvc.exe
kxescore.exe
KVExpert.exe
kxetray.exe
KSafeSvc.exe
KSafeTray.exe
guiyingfix.exe
RavMonD.exe
RsTray.exe
RsAgent.exe
RegGuide.exe
RsMain.exe
RsCopy.exe
Rav.exe
KVSrvXP.exe
KVExpert.exe
KVMonXp.exe
avp.exe
avp.exe
ras.exe
knownsvr.exe
rstray.exe
knsdtray.exe
knsd.exe
knsdsvc.exe
knsdsve.exe
QQPCLeakScan.exe
QQPCWebShield.exe
QQPCTAVSrv.exe
QQPCRTP.exe
QQPCMgr.exe
QQPCUpdateAVLib.exe
QQPCTray.exe
QQRepair.exe
QQPCPatch.exe
Killing processes code:
HTTP-request:
HTTP/1.1
Accept: */*
Accept-Language: zh-cn
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
Host: %s
Connection: Keep-Alive
http://www.kernelmode.info/forum/viewtopic.php?f=16&t=1765#p14683
Dumps of malicious code with some comments by Peter here:
http://www.kernelmode.info/forum/viewtopic.php?f=16&t=1765#p14709
Enjoy.