Kaspersky tdsskiller http://support.kaspersky.com/downloads/utils/tdsskiller.exe
ESET tdlfsreader http://eset.ru/tools/TdlFsReader.exe
tdsskiller first
First, edit options
"Checking TDL FS" to On
Performing scanning..
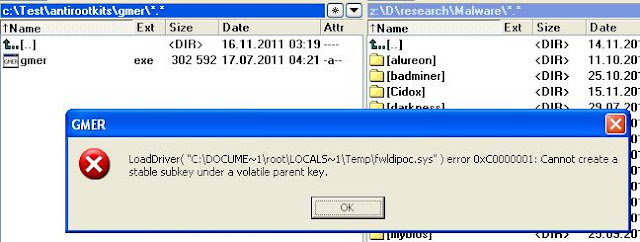
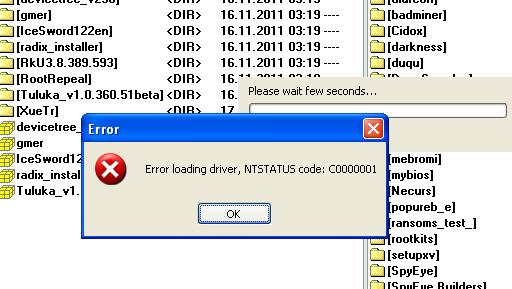
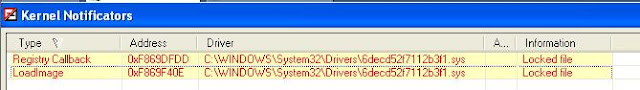
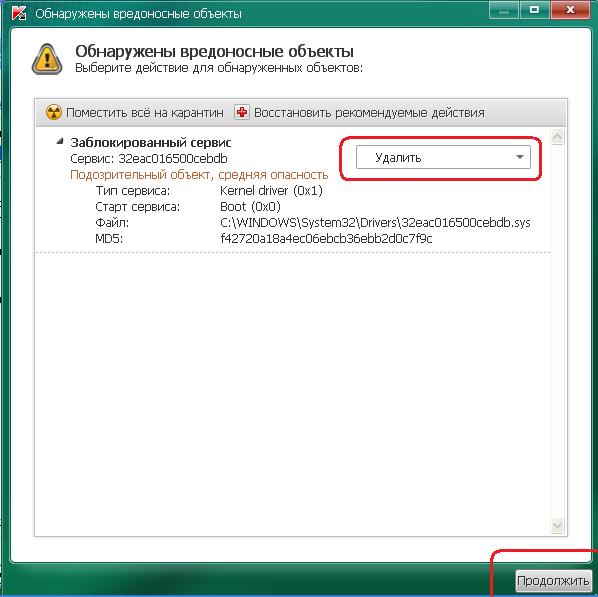
Rootkit was found...
For "TDSS File System" not skip, set to "copy to quarantine"
Go to tdsskiller log in root of system volume, C:
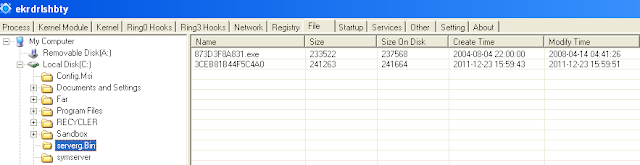
Files of rootkit were saved to %system_volume%:\TDSSKiller_Quarantine\Data_and_Time\.
Try tdlfsreader next
Objects were dumped to TDL_FS dir in current folder.
ESET tdlfsreader http://eset.ru/tools/TdlFsReader.exe
tdsskiller first
First, edit options
"Checking TDL FS" to On
Performing scanning..
Rootkit was found...
For "TDSS File System" not skip, set to "copy to quarantine"
Go to tdsskiller log in root of system volume, C:
Files of rootkit were saved to %system_volume%:\TDSSKiller_Quarantine\Data_and_Time\.
Directory with dumped objects: .dta - dumped objects, .ini - info about dumped object
Objects were dumped to TDL_FS dir in current folder.