As we already know, Microsoft tries to roll out a new security features (aka exploit mitigations) with each release of Windows 10 (RS_X). In previous releases was spotted a built into the OS EMET (aka Exploit Protection), Controlled Folder Access (Anti-Ransom_Encoder), KPTI, IOMMU devices support, Arbitrary Code Guard (ACG), Spectre-related mitigations, etc. A comprehensive list of such improvements could be found in the document Mitigate threats by using Windows 10 security features and presentation of Matt Miller and Dave Weston at BH USA 2016 called Windows 10 Mitigation Improvements.
In this blog post I'll try to describe some new Windows 10 RS5 kernel changes as well as other security features that Microsoft has introduced with this Windows release. Here are some findings: RS5 brings new type of PTE, improves support of Intel's CET technology, offers a special mitigation into the VMM to harden from L1TF vulnerability, introduces so-called Security Domains into the NT kernel.
L1TF mitigation
L1 Terminal Fault is already a well-known vulnerability that is related to speculative execution side channel attacks. But unlike previous Spectre cases, L1TF relies on the fact that speculative execution makes it possible to track data located at a physical page (PFN) that is actually not used in any valid VMM' PTE. In other words, the CPU speculatively addresses to invalid PTE that is still pointing to some PFN while Windows dispatches #PF exception. More details in Matt Miller blog post.
After MS has released a security update for L1TF mitigation, I have checked the ntoskrnl and found a way they fix this vulnerability. As Matt wrote into blog post, the VMM just corrupts PFN fields inside invalid PTE thus if CPU will try to translate this PTE speculatively, it just simply will get fake physical address that points to beyond the borders of memory.
As we know from the VMM internals, Transition PTE type is exactly that type may be used for L1TF attack. The VMM translates valid PTE to Transition state, when it becomes useless for a caller process. For example, process commits memory -> process frees memory (PTE becomes from Valid state to Transition). After Transition state, the VMM set it to another state and leave a note into the PFN database. MS has added MiSwizzleInvalidPte for VMM to corrupt PFN field into Transition PTE.
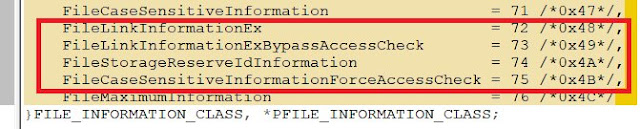
The new FileInfo classes
Windows 10 RS5 introduces new members of famous FILE_INFORMATION_CLASS enumeration that are hinted that you can get access to more information about files in this new Windows release.
- FileLinkInformationEx = 72 /*0x48*/,
- FileLinkInformationExBypassAccessCheck = 73 /*0x49*/,
- FileStorageReserveIdInformation = 74 /*0x4A*/,
- FileCaseSensitiveInformationForceAccessCheck = 75 /*0x4B*/,
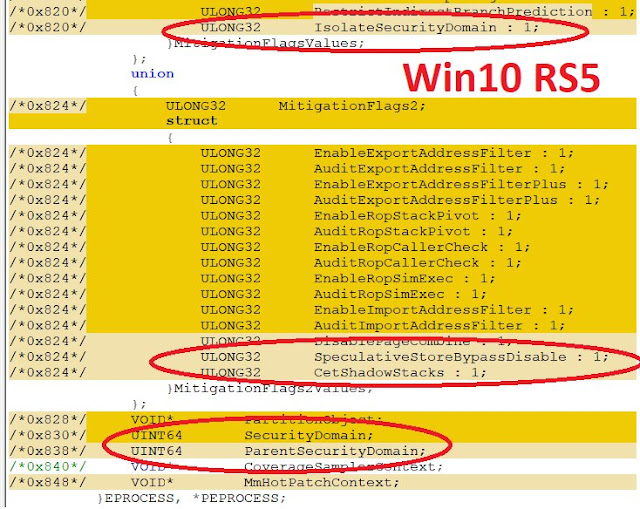
The new types of mitigations
Windows 10 RS5 introduces several new types of subj. You can see it below.
· PS_MITIGATION_OPTION_SPECULATIVE_STORE_BYPASS_DISABLE
· PS_MITIGATION_OPTION_ALLOW_DOWNGRADE_DYNAMIC_CODE_POLICY
· PS_MITIGATION_OPTION_CET_SHADOW_STACKS
First mitigation improves Windows immunity to Speculative Store Bypass (SSB) vulnerability. Second as I think is related to Arbitrary Code Guard (ACG). And third adds support of Intel CET anti-exploit technology.
Security Domains
RS5 also brings an interesting term that I believe may be relevant to SESC attacks too. Now EPROCESS'es could be linked to so-called "Security Domain".
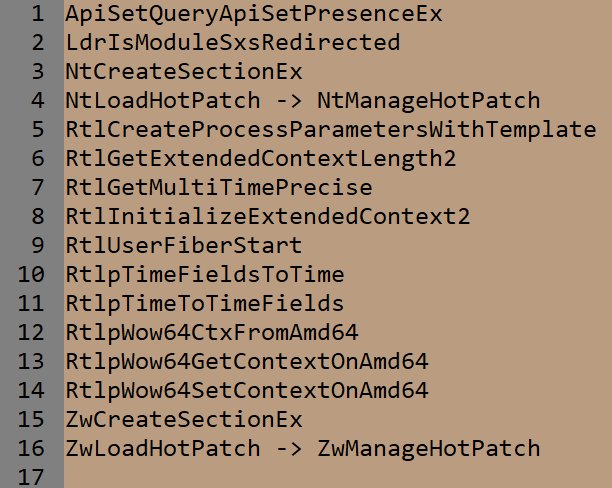
Ntdll welcomes new API.
MACHINE FRAME
For those who had deal with basics Windows NT or Linux internals concepts, the term "frame" is known. It represents set of registers that have been captured at the moment of interruption or exception: trap frame, exception frame are famous instances. When the frame was captured, later interrupt manager, exception manager or system service manager will return a program execution flow to the original state (pre-interruption) using frame info.
Windows 10 RS5 introduces a new type of frame: machine frame. It is used for Processor Control Block (KPRCB) to capture its state when a some sort of interruption occurs.
Retpoline
The Retpoline mitigation practice is well known in the Linux world. This feature has been used to protect apps from Spectre #2 (preventing branch target injection). Windows 10 RS5 says hi to Retpoline too.
Supporting Intel CET mitigation & a new PTE type
RS5 is armed to support the Intel CET technology that is designed to harden a system from ROP-based attacks more effective. CET introduces a special type of thread' stack - shadow stack that is served by silicon itself. The addresses that are pushed to usual stack are duplicated at shadow stack too. Later CPU can compare both and detect potential ROP attack.
"CET defines a second stack (shadow stack) exclusively used for control transfer operations, in addition to the traditional stack used for control transfer and data. When CET is enabled, CALL instruction pushes the return address into a shadow stack in addition to its normal behavior of pushing return address into the normal stack (no changes to traditional stack operation). The return instructions (e.g. RET) pops return address from both shadow and traditional stacks, and only transfers control to popped address if return addresses from both stacks match. There are restrictions to write operations to shadow stack to make it harder for adversary to modify return address on both copies of stack implemented by changes to page tables. Thus limiting shadow stack usage to call and return operations for purpose of storing return address only. The page table protections for shadow stack are also designed to protect integrity of shadow stack by preventing unintended or malicious switching of shadow stack and/or overflow and underflow of shadow stack." @Intel.
CET supporting is deeply integrated into the NT kernel. For example, when thread dies, its shadow stack releases.