Dropper was captured about 3 weeks ago with help of VX Vault.
Hash:
SHA1: 53b1ce48f2b0cf3c7028184676be7b21485bd45a
MD5: ab551ebc28e4cbcdcb44b1175e14038b
File size: 39936 bytes
Threat consists of three components:
- Dropper - extracts two other components and installs in the system.
- Dll - main payload.
- Driver - contains AhnLab-V3 AV killing features.
According to VT in ITW about 4 weeks.
Hash:
SHA1: 53b1ce48f2b0cf3c7028184676be7b21485bd45a
MD5: ab551ebc28e4cbcdcb44b1175e14038b
File size: 39936 bytes
Threat consists of three components:
- Dropper - extracts two other components and installs in the system.
- Dll - main payload.
- Driver - contains AhnLab-V3 AV killing features.
According to VT in ITW about 4 weeks.
Was discussed in brief here [once it was discovered]:
Original dropper packed with UPX and masked as legal (valid version info).
Decrypted dropper:
SHA1: eb00947b3d07510120fa465e5a9f439bc586b618
MD5: abb1bd5e230a78f3946fae840c4fff68
File size: 106496 bytes
26 / 41
I was really surprised that AhnLab-V3 missed verdict of unpacked...
Decrypted dropper stores payload in .rsrc section.
Dropper have a simple obfuscation of code and strings:
Strings obfuscation:
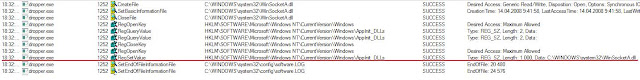
First that dropper performs - extracts driver from resource and writes it into file.
Driver dropped to LOL path - C:\WINDOWSrandom.sys, C:\WINDOWSJytVKZN.sys [in my case].
Second, extracts dll and sets it into autorun via
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs
Autorun:
Driver hash:
SHA1: dc0a214282c96306586ac3dffd1540af3f547d42
MD5: 52d513b5bf0dbbfdc9ecc928415a8457
File size: 5248 bytes
Killing processes algorithm:
Tries to restore hooks on ObOpenObjectByPointer and ObReferenceObjectByHandle (Kernel API, look WDK).
LOL
Dll:
SHA1: fe852d011be23db6d560528bd027f03dcd80274a
MD5: 3ba32ad45dcb77eb14fd375a843f10cc
File size: 72704 bytes
Dll dropped to SystemRoot\System32\WinsocketA.dll (look screen above) and is loaded in every process with help of AppInit_DLLs key. WinsocketA.dll contains all payload of the threat.
As soon as dll is loaded into new process (DLL_PROCESS_ATTACH), it perform checking image name of processes it was loaded.
It performs a special actions for various processes it was loaded.
For example, if dll is running in context of IE, it performs the interception next functions:
WinInet.dll!InternetReadFile
WinInet.dll!HttpWrapSendRequest
kernel32!MultiByteToWideChar
ws2_32.dll!send
Dll's code contains anti-debug features such as function prolog bypassing. Thus, it is invisible for usual breakpoints which are established on the function beginning.
Also dll contains stubs for all export functions of ws2help.dll.
Also DLL uses PEB-modifications technique for hide itself from module list.
ws2_32.dll!send hook:
WinInet.dll!InternetReadFile hook:
It forges some requests and forms and these data are fragmented.
this.AosGetText4 = function (elementObj){var e1=aos_get_text4(elementObj,1);var e2="";if(elementObj.value.length > 12){e2 = aos_get_text4(elementObj,2);}e2=aos_get_text2(elementObj);return [e1,e2];}/*------------------------------------------------------*/
this.AosGetText4 = function (elementObj)
function aos_get_text4(obj,order){var a="";try{a=MKD25.GetText4(obj,order);document.getElementById("sbanner").value=MKD25.GetText2(obj);return a;}catch(e){}return a;}/*------------*/
function aos_get_text4( obj, order )
NgbClientForm.AddChildForSubform( 'strLeftID', %s );
NgbClientForm.AddChildForSubform( 'strLeftPw', %s );
///////////////////////////////////////////////////////
if ( %s == '' )
%[^,]
this.Login = function(
codeRegSite, strRedirect, isPhone )
this.Login = function( _
wlaiq55
</strong>
<span><strong>